FTimes is a system baselining and evidence collection tool.. #System baselining #Evidence collection #System monitoring #FTimes #Baselining #Evidence
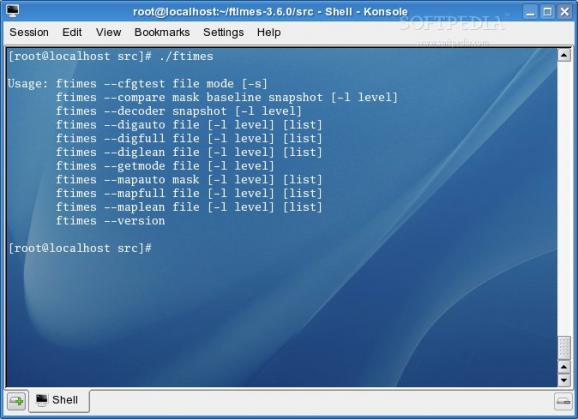
FTimes is a system baselining and evidence collection tool. FTimes's primary purpose is to gather and/or develop information about specified directories and files in a manner conducive to intrusion analysis.
FTimes is a lightweight tool in the sense that it doesn't need to be "installed" on a given system to work on that system, it is small enough to fit on a single floppy, and it provides only a command line interface.
Preserving records of all activity that occurs during a snapshot is important for intrusion analysis and evidence admissibility. For this reason, FTimes was designed to log four types of information: configuration settings, progress indicators, metrics, and errors. Output produced by FTimes is delimited text, and therefore, is easily assimilated by a wide variety of existing tools.
FTimes basically implements two general capabilities: file topography and string search. File topography is the process of mapping key attributes of directories and files on a given file system. String search is the process of digging through directories and files on a given file system while looking for a specific sequence of bytes. Respectively, these capabilities are referred to as map mode and dig mode.
FTimes supports two operating environments: workbench and client-server. In the workbench environment, the operator uses FTimes to do things such as examine evidence (e.g., a disk image or files from a compromised system), analyze snapshots for change, search for files that have specific attributes, verify file integrity, and so on. In the client-server environment, the focus shifts from what the operator can do locally to how the operator can efficiently monitor, manage, and aggregate snapshot data for many hosts. In the client-server environment, the primary goal is to move collected data from the host to a centralized system, known as an Integrity Server, in a secure and authenticated fashion. An Integrity Server is a hardened system that has been configured to handle FTimes GET, PING, and PUT HTTP/S requests.
The FTimes distribution contains a script called nph-ftimes.cgi that may be used in conjunction with a Web server to implement a public Integrity Server interface. Deeper topics such as the construction and internal mechanics of an Integrity Server are not addressed here.
What's new in FTimes 3.10.0:
- The code was cleaned up and refined as necessary.
- Several bugs have been fixed.
- This release includes updated support for file hooks and introduces KL-EL-based XMagic.
- Consequently, the minimum required version of libklel has been rasied to 1.1.0, which has a library version of 2:0:1.
FTimes 3.10.0
add to watchlist add to download basket send us an update REPORT- runs on:
- Linux
- main category:
- System
- developer:
- visit homepage
Zoom Client 6.0.3.37634
Context Menu Manager 3.3.3.1
IrfanView 4.67
4k Video Downloader 1.5.3.0080 Plus / 4.30.0.5655
Microsoft Teams 24060.3102.2733.5911 Home / 1.7.00.7956 Work
7-Zip 23.01 / 24.04 Beta
ShareX 16.0.1
calibre 7.9.0
Bitdefender Antivirus Free 27.0.35.146
Windows Sandbox Launcher 1.0.0
- calibre
- Bitdefender Antivirus Free
- Windows Sandbox Launcher
- Zoom Client
- Context Menu Manager
- IrfanView
- 4k Video Downloader
- Microsoft Teams
- 7-Zip
- ShareX