An open source implementation of the Domain Name System (DNS) protocols, a DNS server and resolver #BIND nameserver #BIND server #Domain Name System #DNS #Nameserver #Server
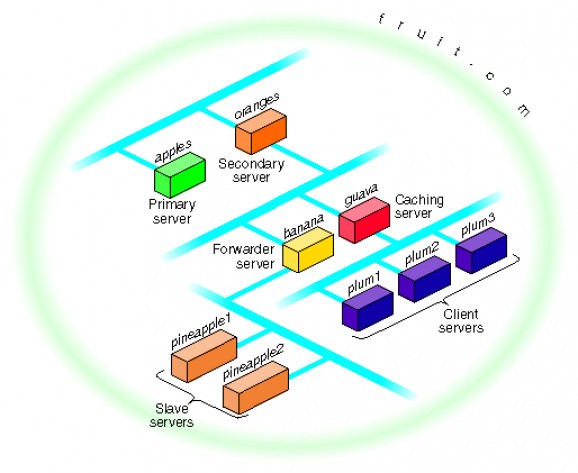
BIND (Berkeley Internet Name Domain) is a command-line UNIX software that distributes an open source implementation of the Domain Name System (DNS) protocols. It is comprised of a resolver library, a server/daemon called `named', as well as software tools for testing and verifying the proper operation of the DNS servers.
Originally written at University of California at Berkeley, BIND was underwritten by numerous organizations, including Sun Microsystems, HP, Compaq, IBM, Silicon Graphics, Network Associates, U.S. Defense Information Systems Agency, USENIX Association, Process Software Corporation, Nominum, and Stichting NLNet – NLNet Foundation.
As mentioned, BIND comprises of a domain name system server, a domain name system resolver library and software tools for testing servers. While the DNS server implementation is in charge of answering all the received questions by using the rules stated in the official DNS protocol standards, the DNS resolver library resolves questions about domain names.
BIND has been specifically designed for the GNU/Linux platform and it should work well with any distribution of Linux, including Debian, Ubuntu, Arch Linux, Fedora, CentOS, Red Hat Enterprise Linux, Slackware, Gentoo, openSUSE, Mageia, and many others. It supports both 32-bit and 64-bit instruction set architectures.
The project is distributed as a single, universal tarball that includes the source code of BIND, allowing users to optimize the software for their hardware platform and operating system (see above for supported OSes and architectures).
BIND 9.15.8
- runs on:
- Linux
- filename:
- bind-9.15.8.tar.gz
- main category:
- Internet
- developer:
- visit homepage
Context Menu Manager 3.3.3.1
Windows Sandbox Launcher 1.0.0
ShareX 16.0.1
IrfanView 4.67
Zoom Client 6.0.4.38135
calibre 7.9.0
Microsoft Teams 24060.3102.2733.5911 Home / 1.7.00.7956 Work
4k Video Downloader 1.5.3.0080 Plus / 4.30.0.5655
7-Zip 23.01 / 24.04 Beta
Bitdefender Antivirus Free 27.0.35.146
- 4k Video Downloader
- 7-Zip
- Bitdefender Antivirus Free
- Context Menu Manager
- Windows Sandbox Launcher
- ShareX
- IrfanView
- Zoom Client
- calibre
- Microsoft Teams